This tool attempts to open a write handle to every registry key in a given hive and reports any successful result. If the key value contains a file, it will attempt to open a write handle to the file and reports any successful result. Also it is probably a bit loud depending on the environment as it will result in a lot of access denials; that said, the tool may not be opsec safe.
I have uploaded a new tool, it is not incredibly robust or feature-rich but I have found at least one vulnerability successfully and therefore deem it useful.
The source code has been pushed to my github here along with a compiled binary under releases.
Overall, it tries to be a straight-forward tool: it attempts to open every single registry key under the specified registry hive and reports on the result of the attempt if it is in fact writeable.
The program will then review all values to see if they contain file extensions within them, if so, it checks if they are in fact a file, and proceeds to try and open those with writeable permissions as well (this can be disabled with the -df flag, more on flags below).
The idea behind this tool is to find writeable locations in registry or associated registry values that you can abuse primarily for privilege escalation; I will go into more info on what you can do with these permissions shortly.
This is a quicker and less sophisticated method than using a more detailed tool like AccessEnum, which will happily dump a wall of information in front of you if that is what you are trying to see.
However, if you are like me, you are just trying to achieve a quick and dirty privilege escalation on a time-boxed assessment and the last thing you want to do is shuffle through a massive haystack for a needle that may not exist.
It was written in C# since I feel that has fairly decent flexibility in how many ways it can be run, reflectively, executable, easily ported to powershell. You can also compile it with something like ExportDLL and use one of many methods by which to load DLLs.
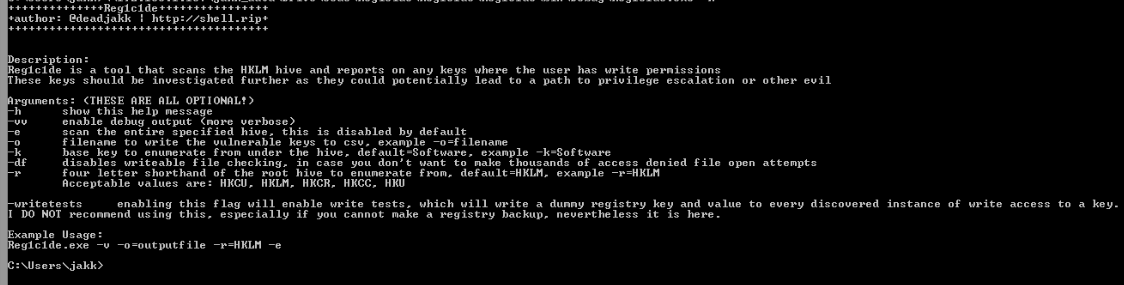
Reg1c1de can be run without any arguments which will cause it to scan everything under HKLM\Software, providing information about writeable registry keys and filepaths that are discovered.
Writes results to a csv file in a better format to parse through
-o=filename
Specifies the root hive from which to begin scanning
-r=HKLM
Specifies the first subkey from the hive to scan, using it as a root.
-k=Software
This flag will scan the entire root hive that you have specified instead of one of it’s subkeys. if this is selected the -k arg is ignored.
-e

The output below shows discovered keys as well as files.
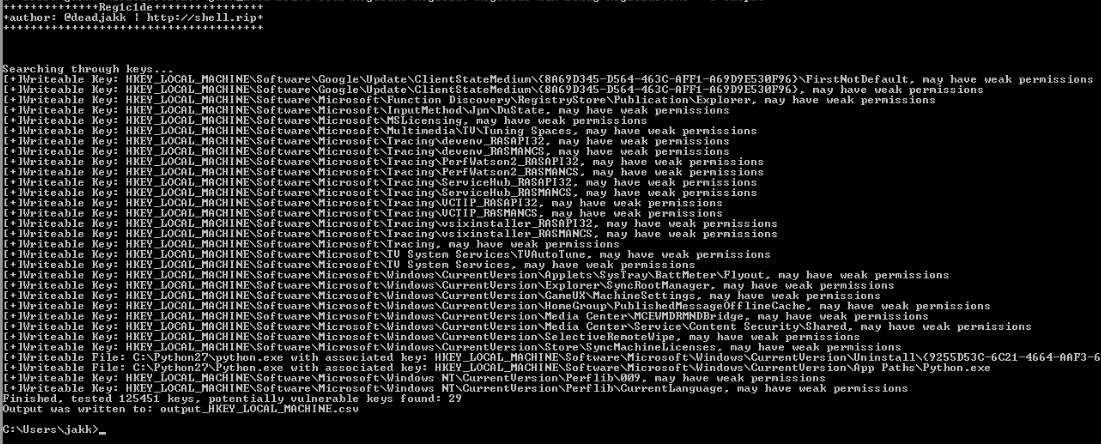
Part of one of Jake Williams's talk on privilege escalation that goes over this sort of attack is here(with timestamp). The registry holds a lot of configuration information for the programs that put them there; things such as “when was this program last run” and “what path do I go to for that dll or binary”. In short, the registry is a massive hierarchical tree of configuration information and if you can modify some key values or any files that those values are referencing, you may be able to steal the box.
Lastly, permissions. The registry has permissions just like basically everything else in Windows, and just like every other permission in Windows, sometimes these are not configured properly. When you find something interesting that you can write or modify, it may get you a privesc, or a vector by which to establish persistence.
One example of this would be a registry key with a value named something like: “ExecutablePath” with the value: “C:\temp\update_workstation.exe”, if you can change this path to something you have access to or even overwrite c:\temp\update_workstation.exe, and the program referencing that path runs as a higher privilege, you may have something. For a more in-depth look into how these things can be abused or general windows privesc, chcek out the video linked in the first sentence of this section
Hopefully this is useful,